An image is all it takes to violate your privacy
When I am with my (not techie) friends, it’s not rare that someone comes up with some story about how mobile phones are listening to our conversations and using that information to target advertising.
I always reply that this is extremely unlikely to happen on an updated OS, because of how the mobile apps permissions model work and also because this would be easily detectable for an expert by monitoring the network traffic. But this explanation is usually not enough to convince my friends, although I usually add that there are countless other ways companies can use to track us (cookies, GPS location, what we post, what we search…).
Unfortunately, the Internet has not been designed with privacy in mind, in fact, all it takes to “break” our privacy is just one simple and innocent image! While this can sound obvious to people working in IT, I noted that the concept sounds mind-blowing to most of the people I explained it to, so I decided to write a blog post to elaborate on it.
So, how can an image be responsible for user privacy?
Well, the “problem” is not the images themselves but is how the HTTP protocol works. This will not be a technical post, so even if you don’t know HTTP deeply, you just need to understand a few key concepts I simplified in this list:
- the HTTP protocol is how machines communicate on the Internet
- when you visit a website from your computer (your own machine), it does an HTTP request to another machine (the server where the website lives), and the other machine responds (if it’s alive) by sending another HTTP request
- an HTTP request comes with some information about the machine, some of it can be redacted (or spoofed!) and others can not
This is a more visual explanation:
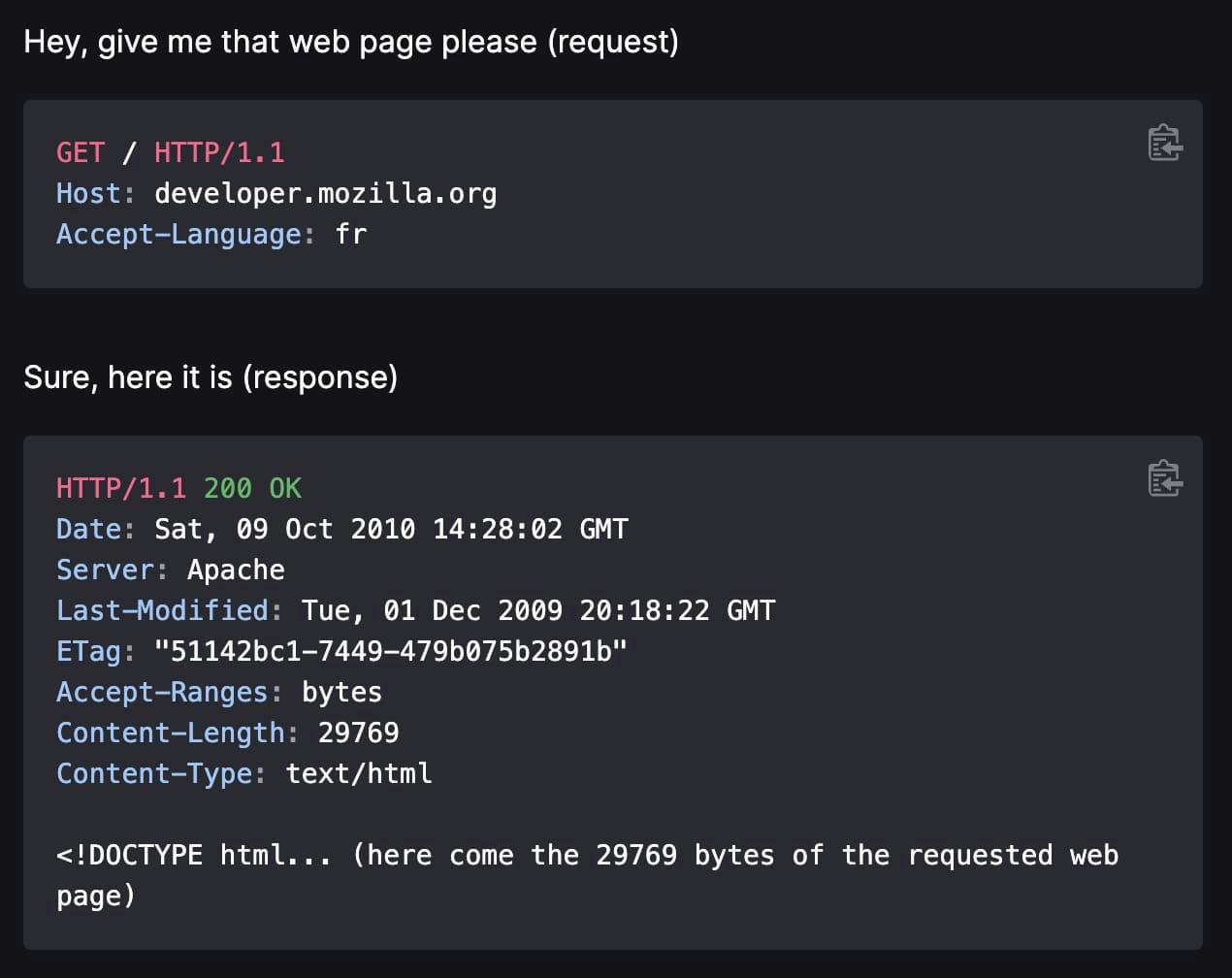
With this basic understanding, let’s consider a very common scenario for everyone: you receive an email with an image inlined in the body or in the signature (not attached). In that case, the image does not “live” in the email itself, but is hosted on a server and called via HTTP from your email client (the software you use to read emails).
At the very moment that you load that image, you have already given away a set of private information that you may not want:
- first, the sender of the email (in theory) knows that you opened the email with 100% accuracy
- unless you are using a VPN, you reveal your IP which comes with other juicy information
- the “User-Agent” which contains information about the device you used to open the email
Now, let’s focus on the IP for one second, what is the juicy information we mentioned a second ago? You can try it yourself on services like ipinfo.io, insert your IP and you will see a whole set of information revealed:
As you see, the IP can be geolocated so you are giving away your location as well, all with an innocent image loaded. Fortunately, IP geolocation is not always very accurate and sometimes can place you miles away, but there are also cases when it can place you in a city with 50/70% accuracy. Isn’t it scary enough? read on!
How can someone know it’s “really me” to open that email?
Super easy! What if that specific image is only present in the email sent to you? Then all HTTP requests coming to that image are all email opening actions from you! In fact, there was even an email client with this specific feature built-in, and the first “spy-pixel” dates back to many years ago.
But it gets worse.
What we explained until now for images in the email it can be called an “embed”. The image lives on his server and it’s embedded in the email. The same mechanism is valid for all the embeds, so in theory, every time a website embeds:
- a YouTube video
- a tweet from Twitter
- a Facebook post
Those are all HTTP requests going from your device to YouTube, Twitter, and Facebook servers with all the information mentioned above, but with a big difference: those corporations can cross-check the information provided (like the IP) with all the info they already have about you and identify a user and his browsing history in a much more exact way.
I am not saying they do, I am saying they could do it!
Ok, now it got scary, right? But wait again, it gets worse.
Don’t forget the dark web
Have you ever wondered how a “data leaks” file looks on the dark web? It may vary of course, but it can also get as simple as a comma-separated list:
ID, username, email, password, address, IP, last access, ...
What about if your IP is a leaked database? It can be matched to your password, which may still be valid. And it can allow criminals to impersonate you on the web. Game over.
Of course, this is really the worst scenario, but it is absolutely possible.
Now, back to the phones listening to us, do you see how is not worth it? All the effort and resources to listen, record, and elaborate with complex and expensive speech-analysis software… just to show an AD?
It’s much easier to gather valuable information on the Internet, “It just takes an image”… maybe that’s why the Facebook tracking software is called “Pixel”!
Almost forgot, how do you protect yourself?
Protecting your privacy online nowadays is not easy, and for sure it deserves a dedicated blog post. But after all these warnings, the minimum I can do is to give you some quick and effective tips:
- use a privacy-focused email service. I personally use ProtonMail which blocks images from being loaded and automatically blocks all the other email trackers. It also comes with strong encryption, to prevent any unauthorized actor from reading your messages.
- if you don’t wanna change your email service, on almost every service there is an option to block the automatic loading of images. Activate it!
- always use a VPN (virtual private network) while surfing the web. A VPN creates a secure tunnel between your device and “the Internet”, and makes sure that your IP doesn’t get disclosed. A VPN is also a good layer of protection when you are on a shared network, where potentially someone else can “overhear” your traffic.
- use DuckDuckGo as a search engine. Apart from keeping your search queries private, it also blocks 3rd parties tracking scripts (like G Analytics, FB Pixel, Taboola, etc…).
With these three tricks, you are already well protected. But if you have to pick up only one, I would go for the VPN.
Wish you safer browsing!